Last weekend was definitely not a normal weekend. The flare out of the computer worm virus WannyCry[1] screwed lot of people’s weekend. It’s been quite long since last mass computer virus outbreak which I can remember was the Blast worm virus[2] back in 2003.
The virus takes advantage of the exploit MS17-010[3] in Windows’ SMB server, it use port 445 to get control of an unpatched computer, and then use this computer to infect more computers on the network. This time, the exploit affects almost every PC running Windows.
Especially for the PC still running outdated version like Windows XP which is widely used in my local banks, companies, stores, gov departments …, etc. Microsoft released a patch[4] for these end-of-life OSes on May 12th, which is very unusual.
Not like the end-of-life OSes, Microsoft has already released patch for Windows Vista and later systems in March. Even though, some of the organizations may have already upgraded to newer operating system (like Windows 7), but for various reasons still not have the exploit patched, and with misconfigured firewall or unrestricted user account privilege, this is a perfect hotbed for the virus. Just need one computer in local area network get infected, and then the virus will start to spread very fast — like plague.
I have already patched all Windows computers in my organization a month earlier, and have all the Windows 10 computers upgraded to Creators update (1703). I double checked the computers and networks again after the break out, just to make sure they have been configured correctly, and have SMBv1 disabled[5]. Better safe than sorry, especially under such circumstances.
Speaking of the virus, it exploits the flaw (EternalBlue[6]) of the Microsoft’s implementation of SMBv1 protocol. Over the years, there have been many security vulnerabilities of this protocol[7] [8] [9], and Microsoft also keeps suggesting user to get rid of deprecated SMBv1 protocol[10] [11].
But what I found interesting is, even in the recently released Windows 10 1703, the operating system still have SMBv1 installed by default. Perhaps this is in consideration for back-ward compatibility with older version Windows and third-party systems, like a NAS. After more digging, I found Windows has already supported SMBv2 since Vista, and third-party system, like Samba has introduced SMBv2 support in 2011[12]. From the 2016 desktop operating system market share chart[13], you can see among the five widely used Windows releases, Windows XP still takes more than 10% market share. Since 2017, more shares have been taken by Windows 10, but Windows XP still gets about 9% share. This might be the reason that Microsoft keeps install SMBv1 in modern release by default, but it still seem a little unnecessary to me.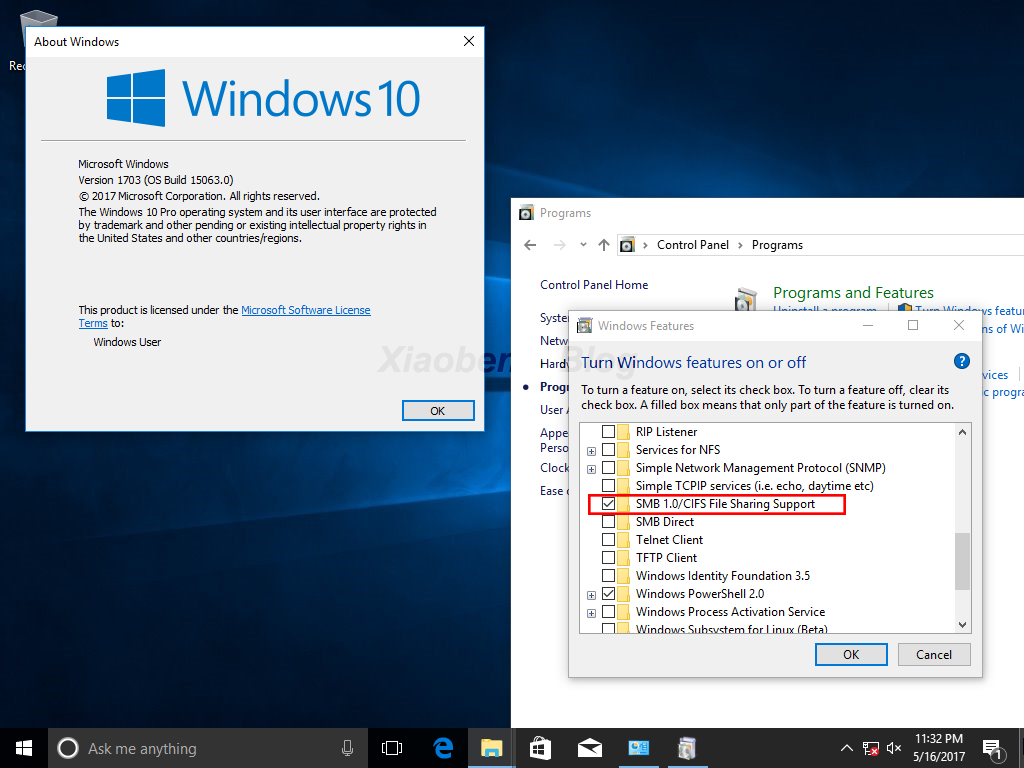
(Windows 10 1703 with SMBv1 support installed by default)
Besides, as far as I know some companies doesn’t have specialized IT staff or doesn’t take information security seriously, this makes them even harder to maintain a safer IT environment and vulnerable to security threats.
Last, to achieve better information security, there are no shortcuts. Here are some of my suggestions:
- Limit user account’s privilege.
In Windows, it’s preferred to use Standard User account type for daily task. In Linux, it’s preferred to prevent remote login as root. - Disable or limit some of the network feature of your network, like UPnP, unless you have software require this to work.
- Set-up proper firewall rules block specific port if necessary.
- Update your software regularly.
Information security is a war that never ends, we can do is to learn from every case, to learn from failure, so that we can be prepared for the uncertain future.
[3] https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
[4] https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
[5] https://support.microsoft.com/en-us/help/2696547/
[6] https://en.wikipedia.org/wiki/EternalBlue
[7] https://technet.microsoft.com/en-us/library/security/ms02-070.aspx
[8] https://technet.microsoft.com/en-us/library/security/ms09-001.aspx
[9] https://technet.microsoft.com/en-us/library/security/ms16-114.aspx
[10] https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
[11] https://blogs.technet.microsoft.com/josebda/2015/04/21/the-deprecation-of-smb1-you-should-be-planning-to-get-rid-of-this-old-smb-dialect/
[12] https://en.wikipedia.org/wiki/Samba_(software)#Version_history
[13] https://www.netmarketshare.com/operating-system-market-share.aspx?qprid=10&qpcustomd=0&qpsp=2016&qpnp=1&qptimeframe=Y